Ars Technica recently ran a story about how University researchers have been able to eavesdrop on LTE mobile phone calls using a USRP B210 software defined radio which runs the Airscope software. The technique exploits a flaw in how some LTE carriers are implementing their keystream. A keystream is a stream of random data combined with the actual voice data, resulting in encrypted data.
It turns out that many LTE carriers reuse the same keystream when two calls are made within a single radio connection. An attacker can then record an encrypted conversation, then immediately call the victim after that conversation. The attacker can now access the encrypted keystream, and as the keystream is identical to the first conversation, the first conversation can now be decoded.
The Ars Technica article, the original paper and a website created about the ReVoLTE technique and software go into detail about how the attack works. On the website the team explain the attack in simple terms:
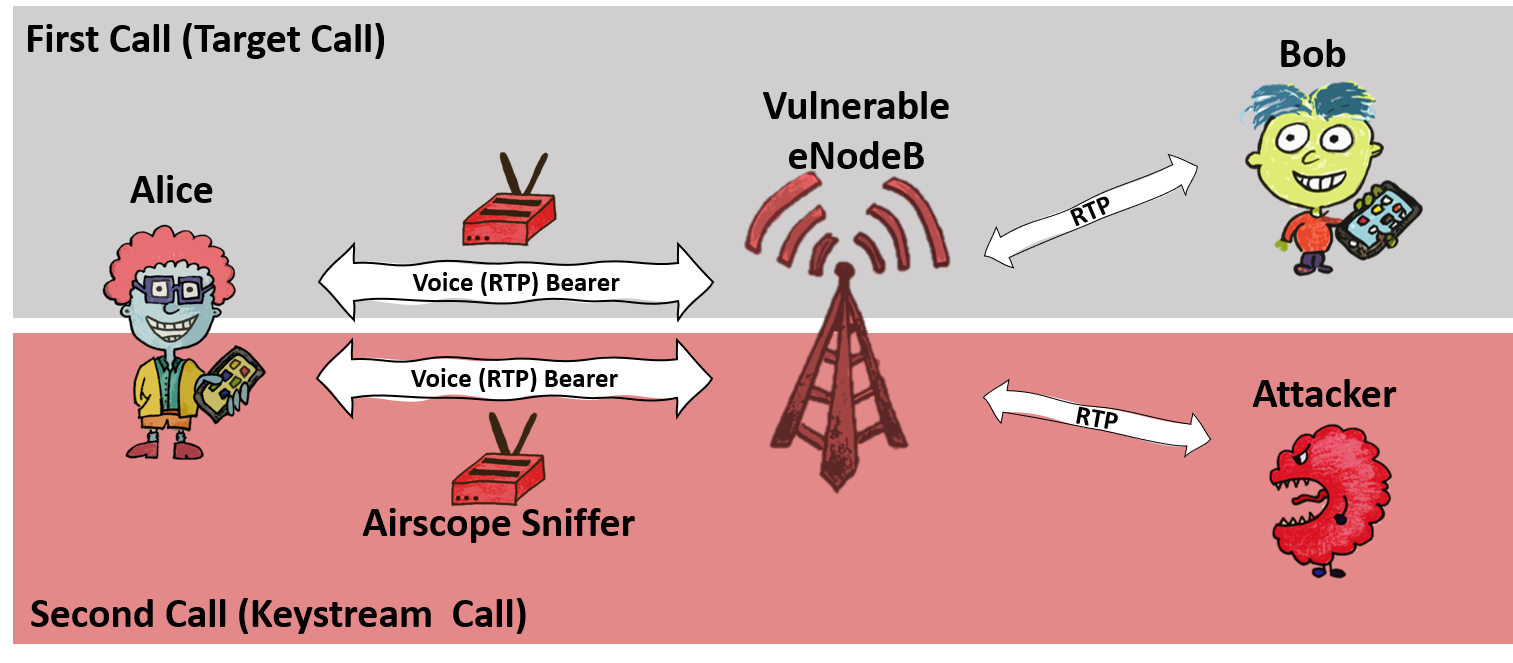
The ReVoLTE attacks exploit the reuse of the same keystream for two subsequent calls within one radio connection. This weakness is caused by an implementation flaw of the base station (eNodeB). In order to determine how widespread the security gap was, we tested a number of randomly selected radio cells mainly across Germany but also other countries. The security gap affected 12 out of 15 base stations.
The ReVoLTE attack aims to eavesdrop the call between Alice and Bob. We will name this call the target or first call. To perform the attack, the attacker sniffs the encrypted radio traffic of Alice within the cell of a vulnerable base station. Shortly after the first call ends, the attacker calls Alice and engages her in a conversation. We name this second call, or keystream call. For this call, the attacker sniffs the encrypted radio traffic of Alice and records the unencrypted sound (known plaintext).
For decrypting the target call, the attacker must now compute the following: First, the attacker xors the known plaintext (recorded at the attacker's phone) with the ciphertext of the keystream call. Thus, the attacker computes the keystream of the keystream call. Due to the vulnerable base station, this keystream is the same as for the target (first) call. In a second step, the attacker decrypts the first call by xoring the keystream with the first call's ciphertext. It is important to note that the attacker has to engage the victim in a longer conversation. The longer he/she talked to the victim, the more content of the previous communication he/she can decrypt. For example, if the attacker and victim spoke for five minutes, the attacker could later decode five minutes of the previous conversation.